JEEMAK Vision 4K - teardown and pwn
Photos of the boards
Front side
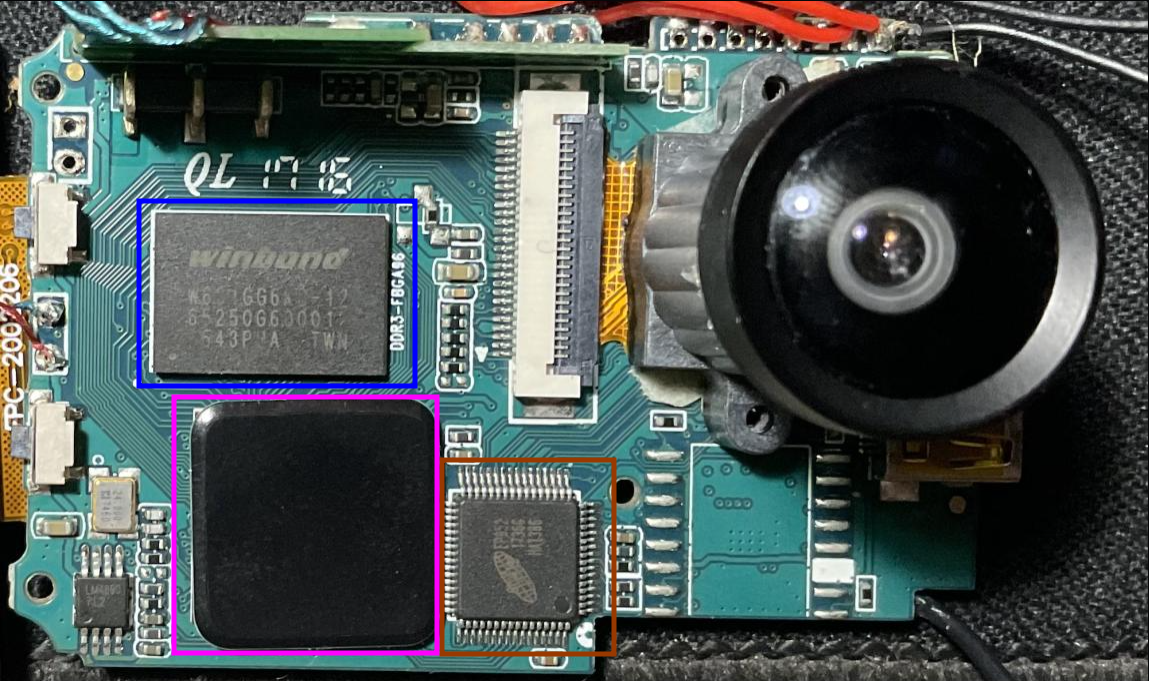
Main components of the front side
EP951 : HDMI interface :
W631GG6KB : IC DRAM 1GBIT :
Allwinner_V3 : ARM CPU : (discovered after removing the black cover)
Back side
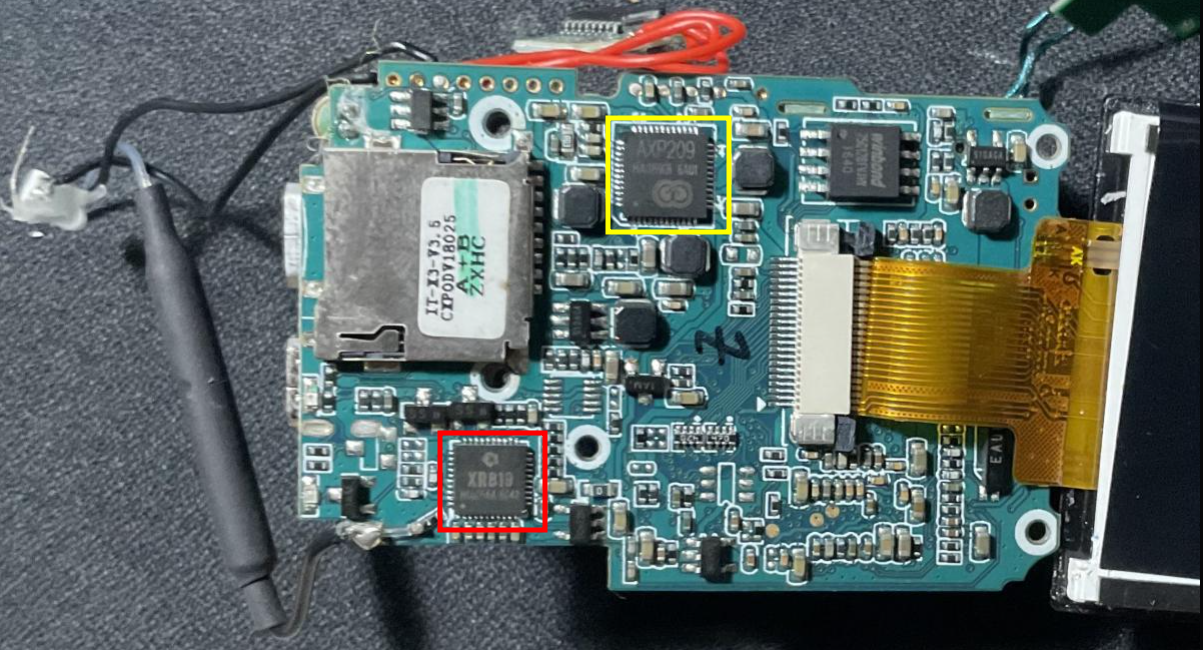
Main components of the back side
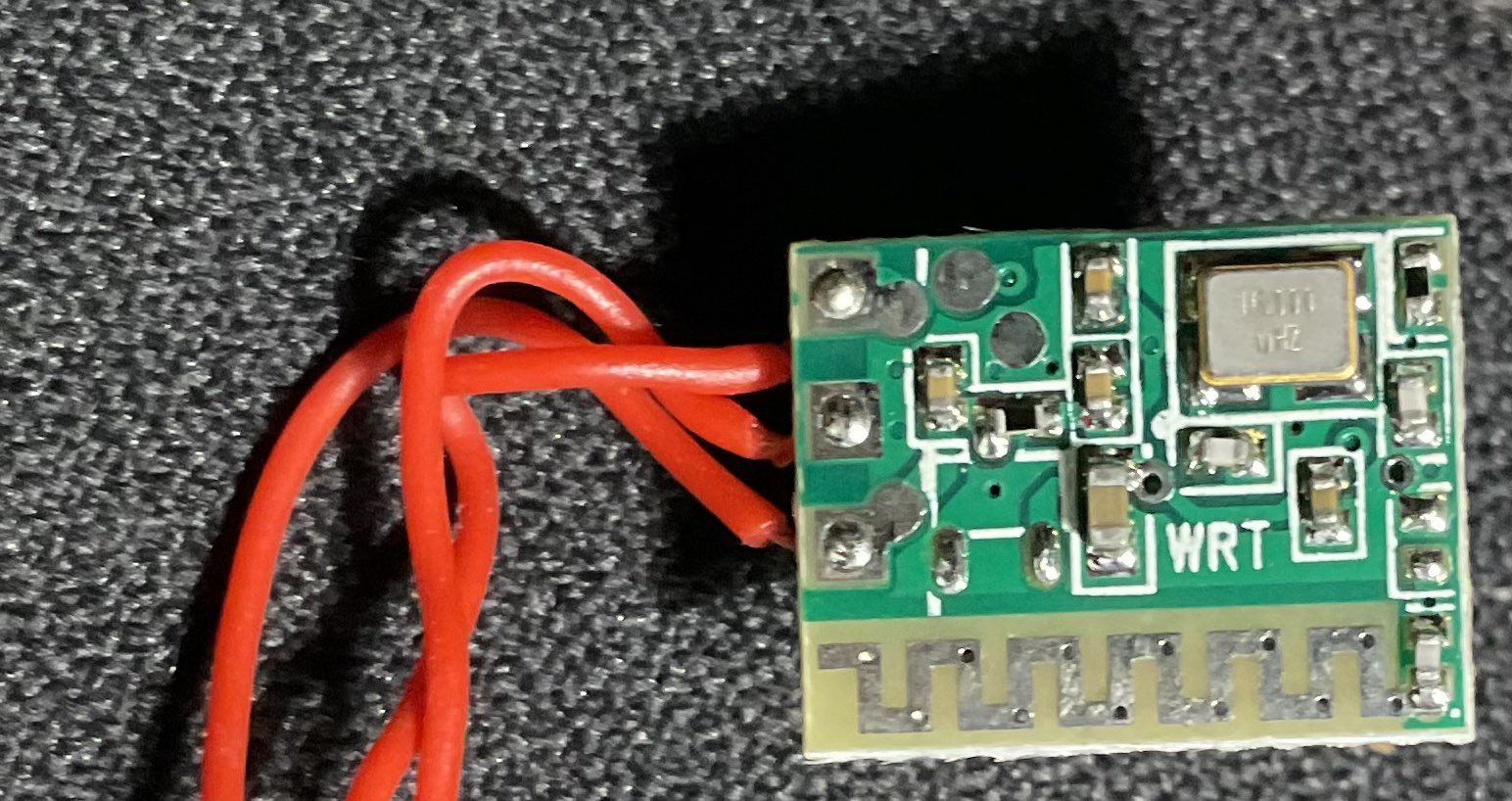
XR819 : Single-Chip IEEE 802.11 b/g/n WLAN
AXP209 : single Cell Li-Battery and Power System Management IC :
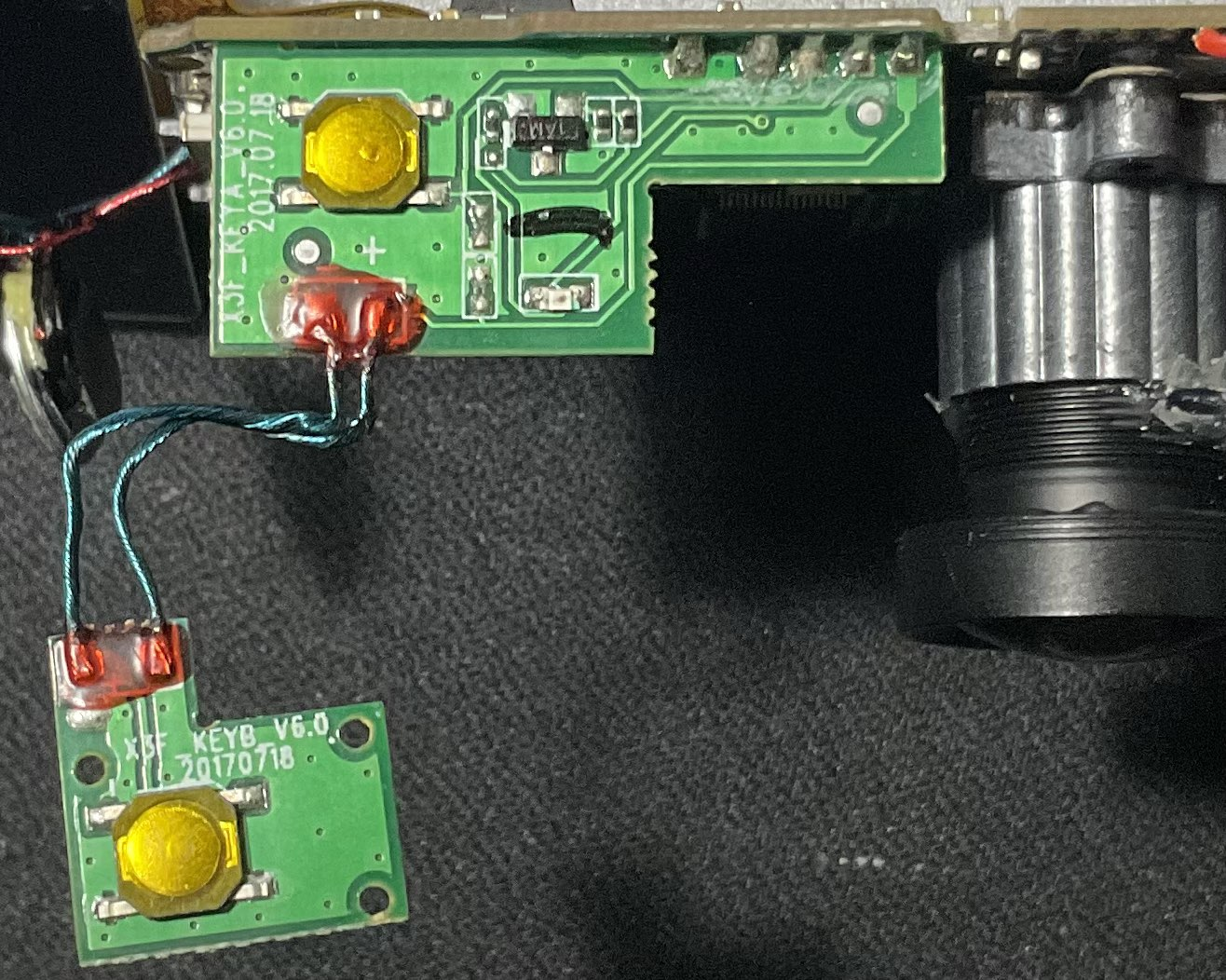
Other boards of the device
Trying to find debug / serial interface
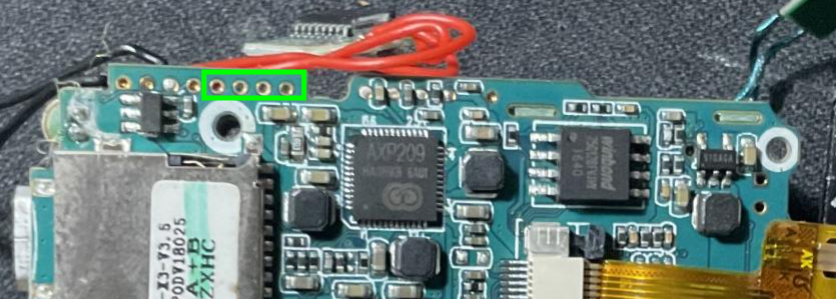
One of the first thing I would like to find is a debug or a serial interface so I could interact with the ARM processor and maybe gain access to it. To do so, I looked at the main board and notices 4 pins that seems to be not in use but still present.
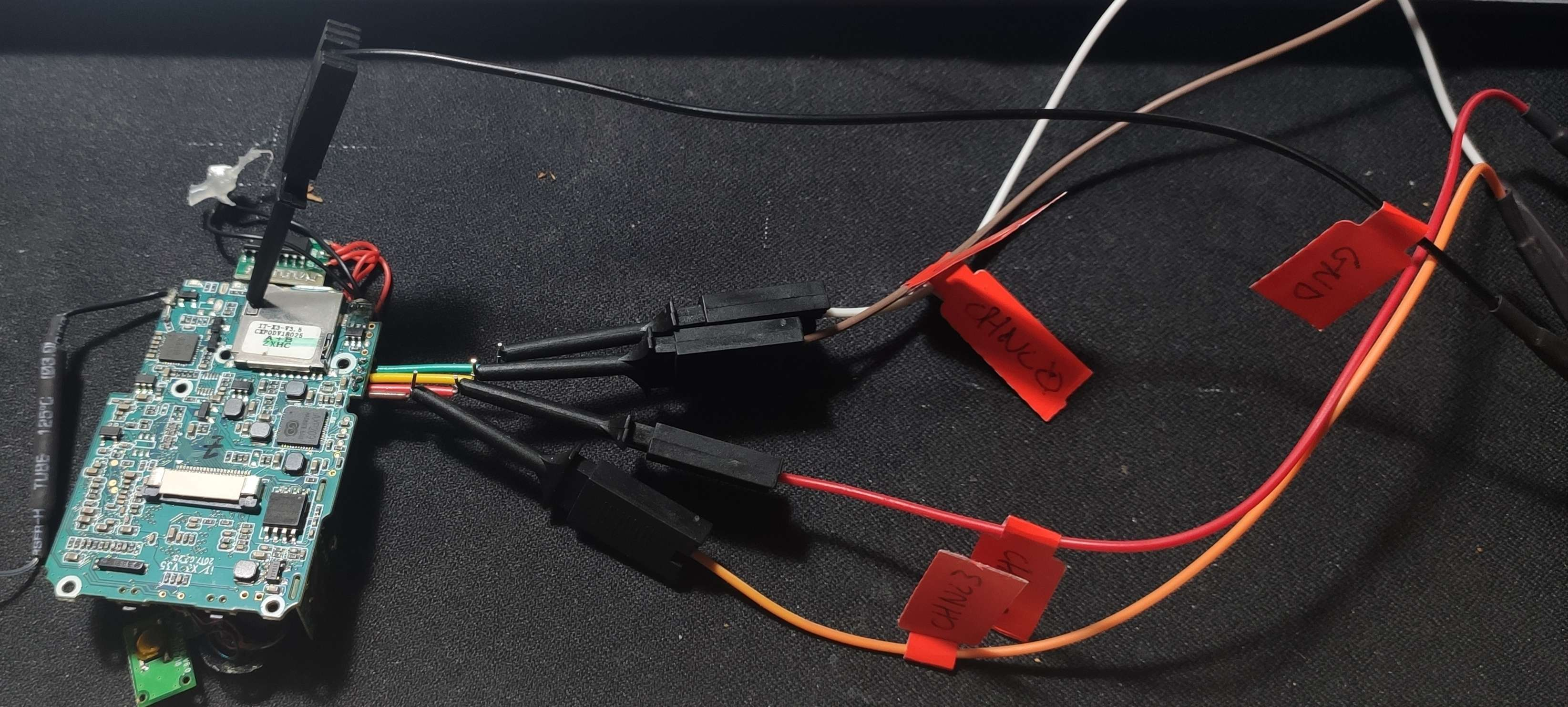
I soldered some cables to it and hoocked up the logic analyser to see if anything goes through it
Now, let’s fire the logic analyser software and plug the device to see if anything come out from one of those pins
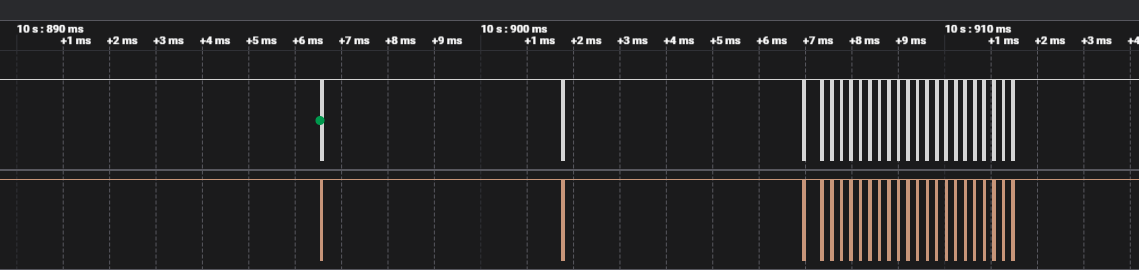
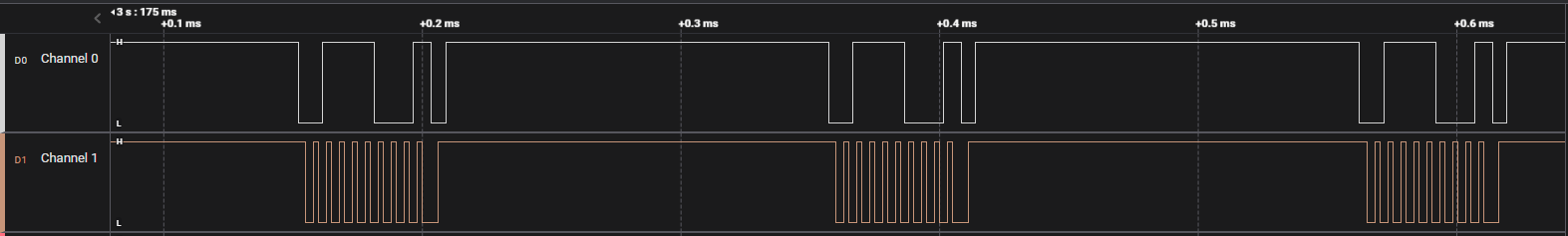
Two other things that have to be determined is the frequency of the communication and the protocol they use (Serial, I2C) but I’m not sure if it would lead somewhere interesting since all the signals appear to be the same just played multiple times.
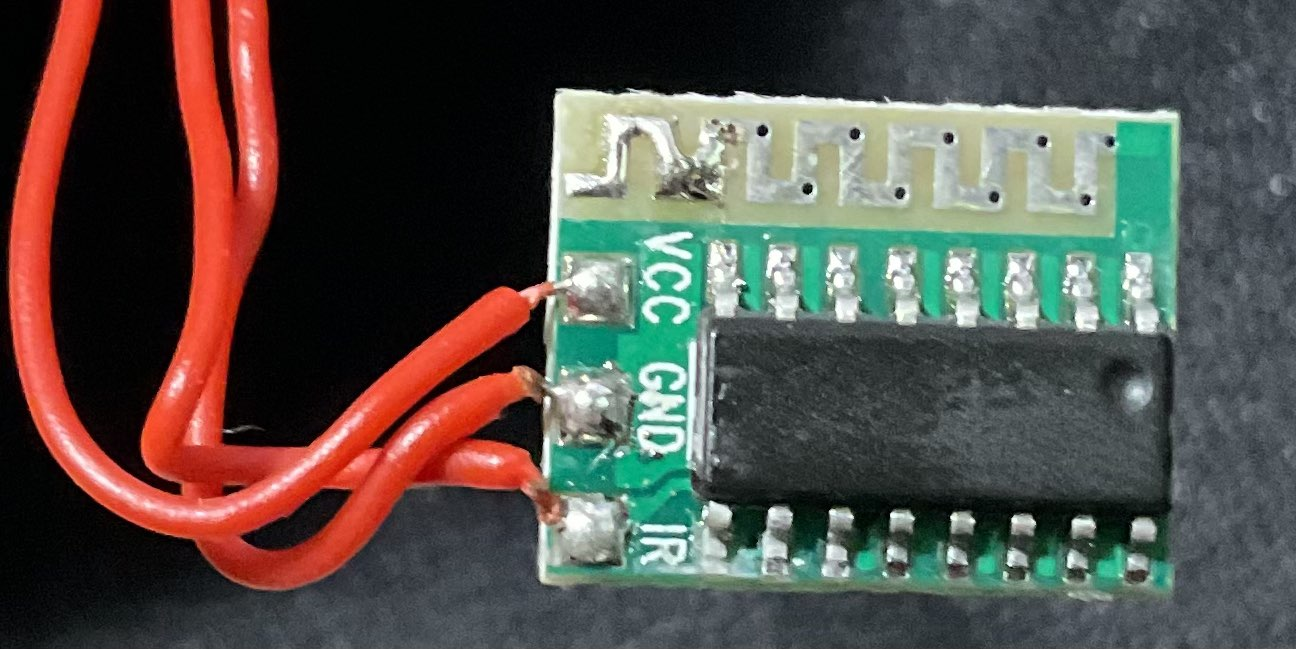
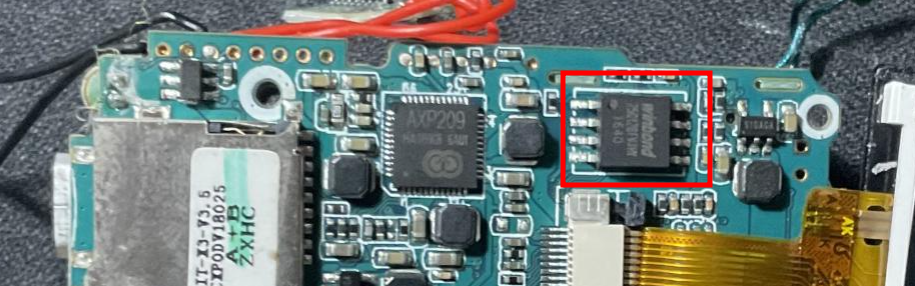
Let’s take a look at the EEPROM
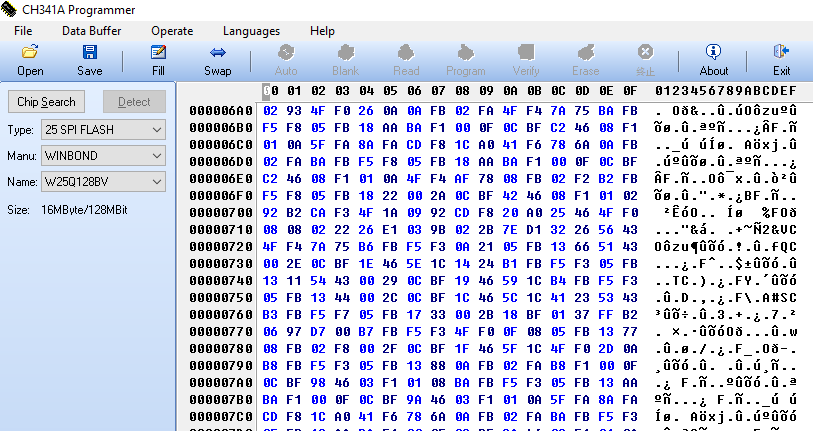
After being unsuccessful at reading informations from the different pins that are on the board, I decided to take a new look at it at try another way to break in. That’s where I found the EEPROM on the board it appears to be a Winbond W25Q128FW.
I plugged it to the CH341A and red it through it’s software and it looks quite promising.
The complete binary file can be found at the following link
Binary analysis
Now that I have the firmware in a bin file, I pushed it into a Kali linux VM to see what I could get from it.
Looking at the content of the .bin file
I first made a binwalk of the file to get an idea of what it contains using
binwalk <file.bin>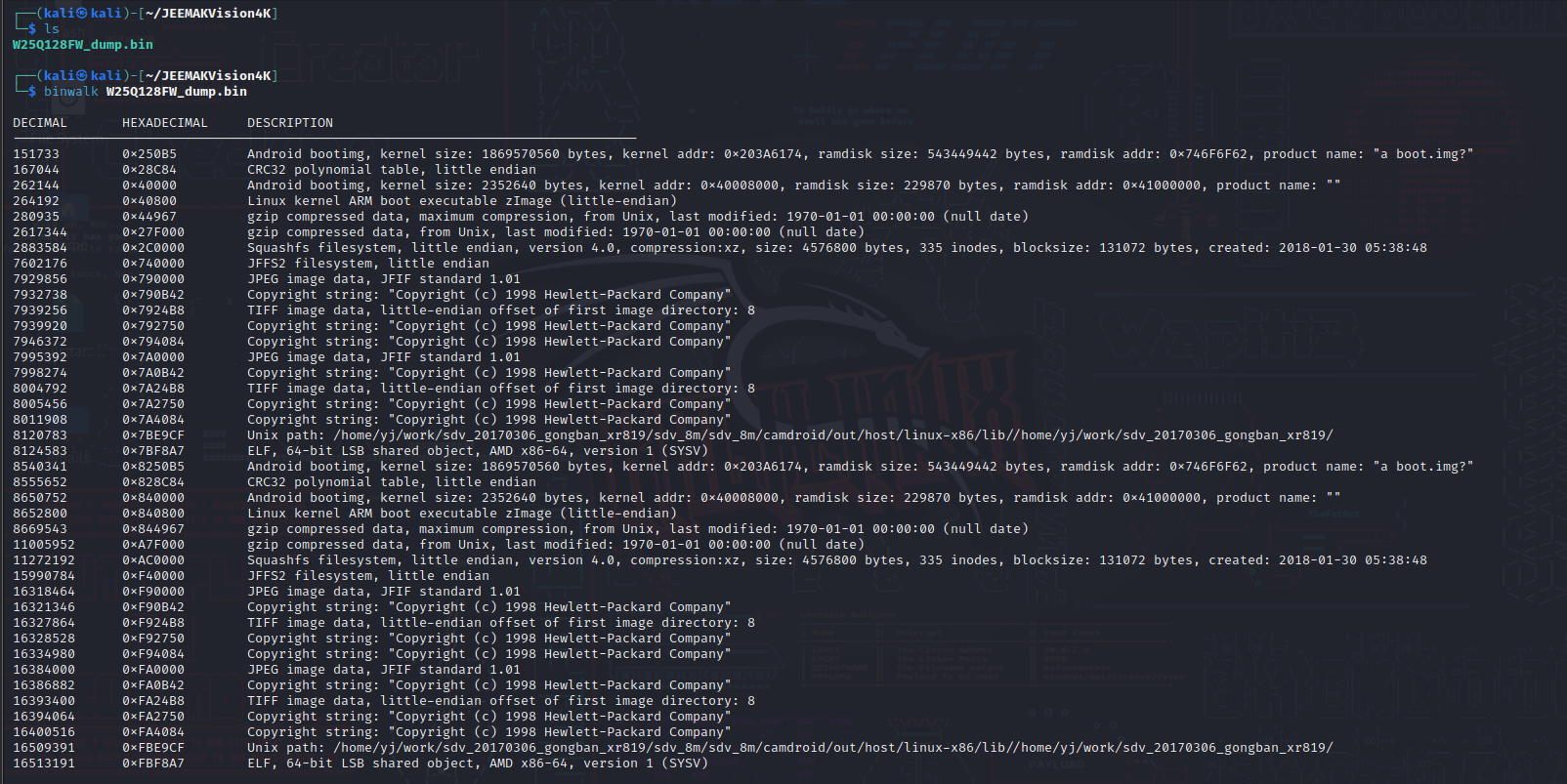
Extracting the data
I then extracted all this to get a closer look at the files that could be interesting using
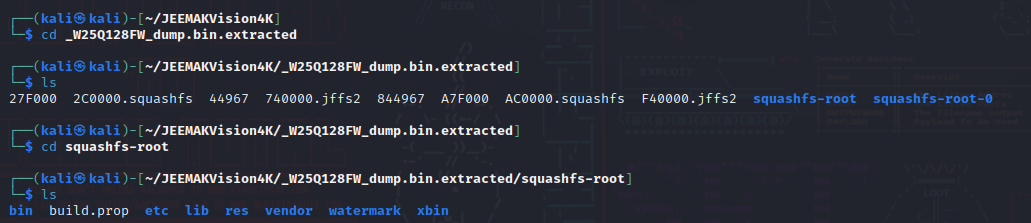
One of the interesting things I saw while extracting the content of the bin file was this line
151733 0x250B5 Android bootimg, kernel size: 1869570560 bytes, kernel addr: 0x203A6174, ramdisk size: 543449442 bytes, ramdisk addr: 0x746F6F62, product name: "a boot.img?"This mean the device would be running under some kind of android ? that could be interesting to test, but first let’s try to see if we can find some informations
Browsing the data
Finding informations about the WiFi
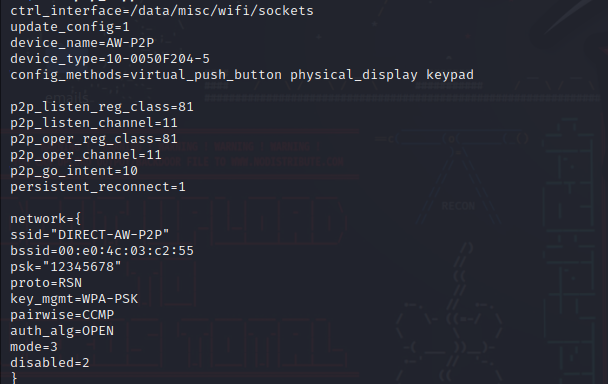
In the path _W25Q128FW_dump.bin.extracted/squashfs-root/etc/wifi It is possible to find a file called p2p_supplicant.conf This file contains some informations like the Channel, SSID, BSSID, and the PSK of the network amongst other things
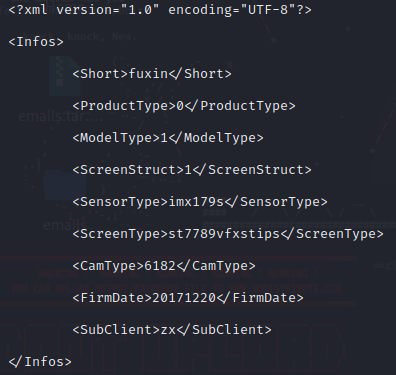
Get some information about the components of the camera
Looks like they reused some code from others manufacturers
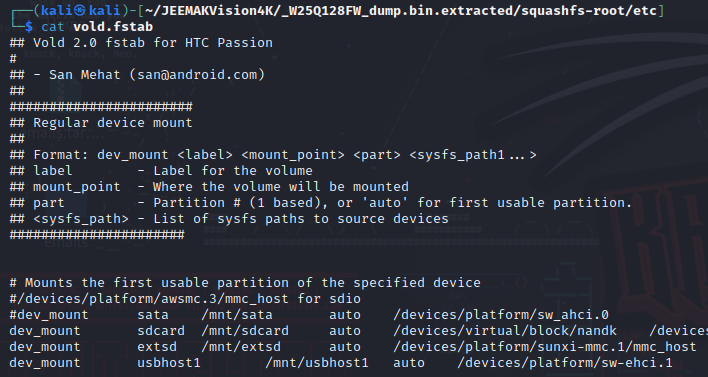
In vold.fstab it is possible to see some references to HTC Passion. I took a look online as I had no idea of what it could be linked to. Turns out this is the code name of the HTC Nexus One
Turns out they also used some of the HTC Nexus One code for the WiFi part of their device
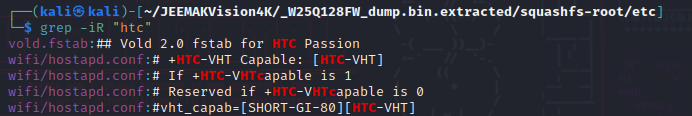
It even is inside FreeBSD code
Some functionnalities still available
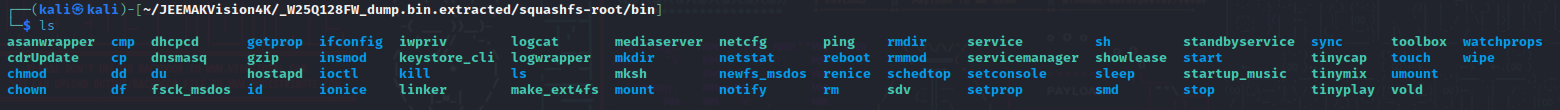
More android structure
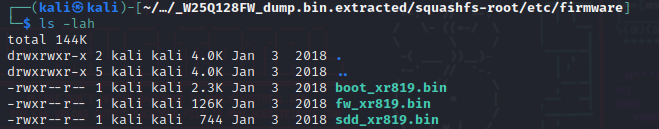
The idea that the device is actually running android seems interesting, the line I noticed earlier makes it really possible, the informations that can be found in the directory _W25Q128FW_dump.bin.extracted/squashfs-root/etc/firmware are also helping with this theory.
Let’s exploit the device as an Android device through ADB
Find the device
From what has been saw previously, this device seems to run under android. Let’s try some shenanigans using ADB to mess around with it !
I plugged it over the USB cable and nothing happened we I plugged the camera, I decided to plug back the screen to the logic board to see if any informations could be provided, it happens that I had to select the USB mode to get access to the camera over USB. And this is what it displayed in VMWare Workstation :
I then started by listing the devices that are available with
adb devices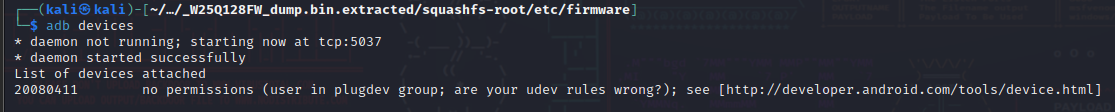
Dump the firmware
I can download the most interesting files with the following commande from ADB
adb pull /dev/block/mtdblock0 uboot.img # uboot
adb pull /dev/block/mtdblock1 boot.img # kernel
adb pull /dev/block/mtdblock2 system.img # squahfs
adb pull /dev/block/mtdblock3 config.img # /data
adb pull /dev/block/mtdblock4 boot-logo.jpg # boot logo
adb pull /dev/block/mtdblock5 shutdown-logo.jpg # shutdown logo
adb pull /dev/block/mtdblock6 env.img # uboot params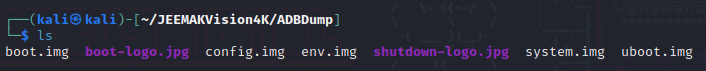
The content of the firmware can be found at the following link :
Exploit the device
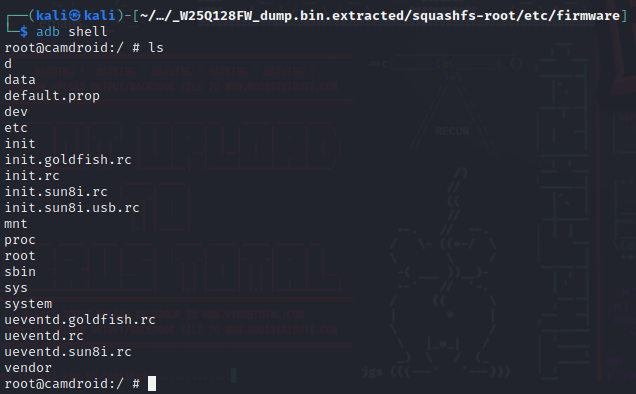
I can now join the shell of the device using
adb shell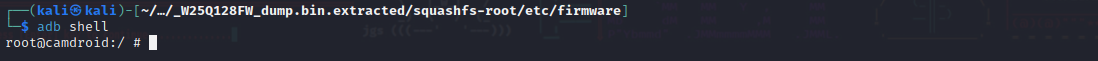
It gives a root shell, from here it could be possible to do anything on the device


 https://www.winbond.com/hq/support/documentation/levelOne.jsp?__locale=en&DocNo=DA00-W25Q128FW.1
https://www.winbond.com/hq/support/documentation/levelOne.jsp?__locale=en&DocNo=DA00-W25Q128FW.1