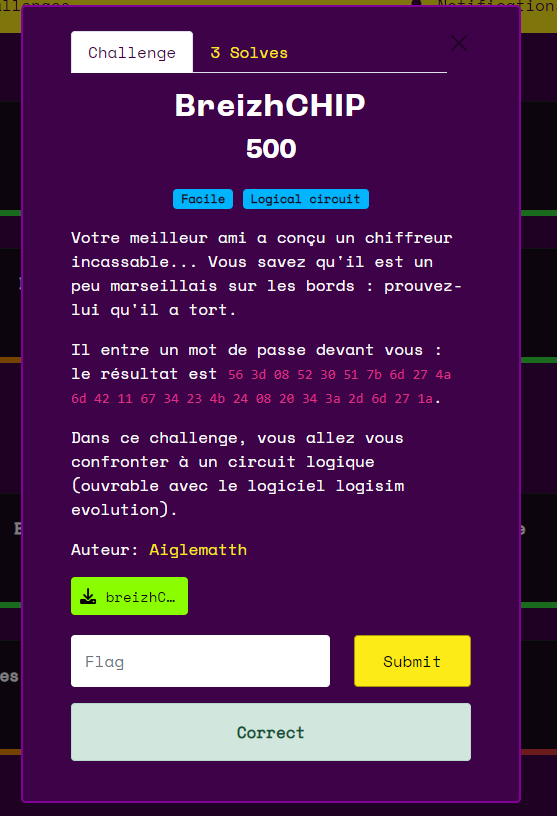
breizhctf-2023 : breizhCHIP
Challenge instructions and file
 https://github.com/BreizhCTF/breizhctf-2023/tree/main/challenges/reverse/breizhCHIP/Challenge
https://github.com/BreizhCTF/breizhctf-2023/tree/main/challenges/reverse/breizhCHIP/ChallengeStep 1 : Get the software to open the file
As explained in the challenge, we need to get our hands on logisim evolution, the software can be found at the following link :
 https://github.com/logisim-evolution/logisim-evolution
https://github.com/logisim-evolution/logisim-evolutionStep 2 : open the file and take a look
Step 2-A : get scared
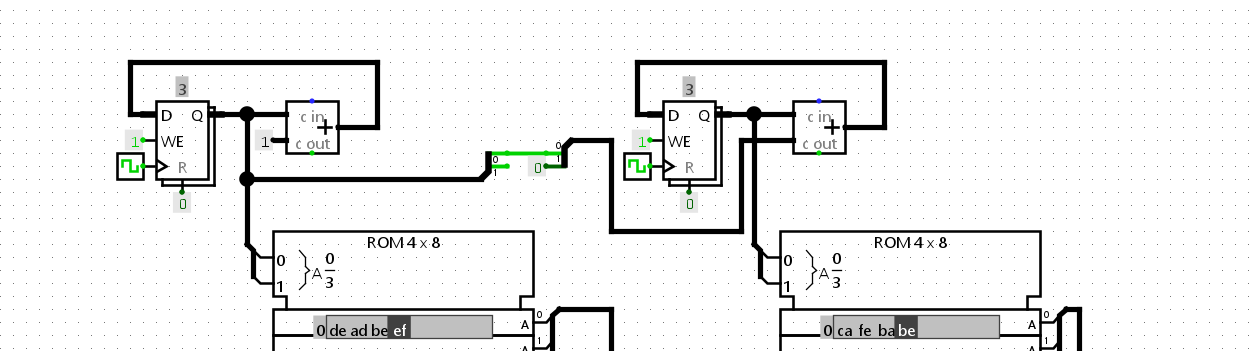
Once we open the file we are facing some electronic schematics. My first taught was to reverse it to make it the way around to give us back the entered value.
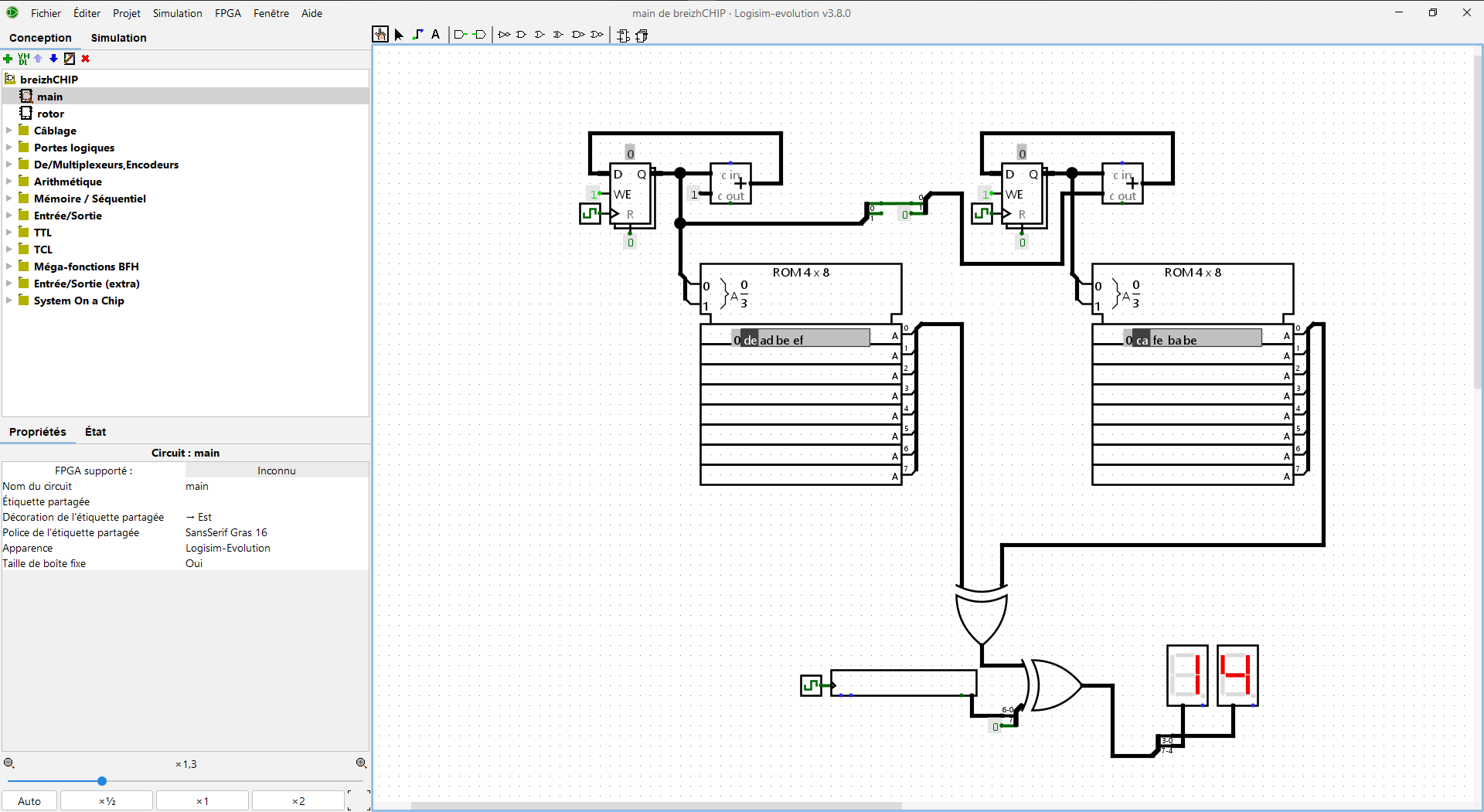
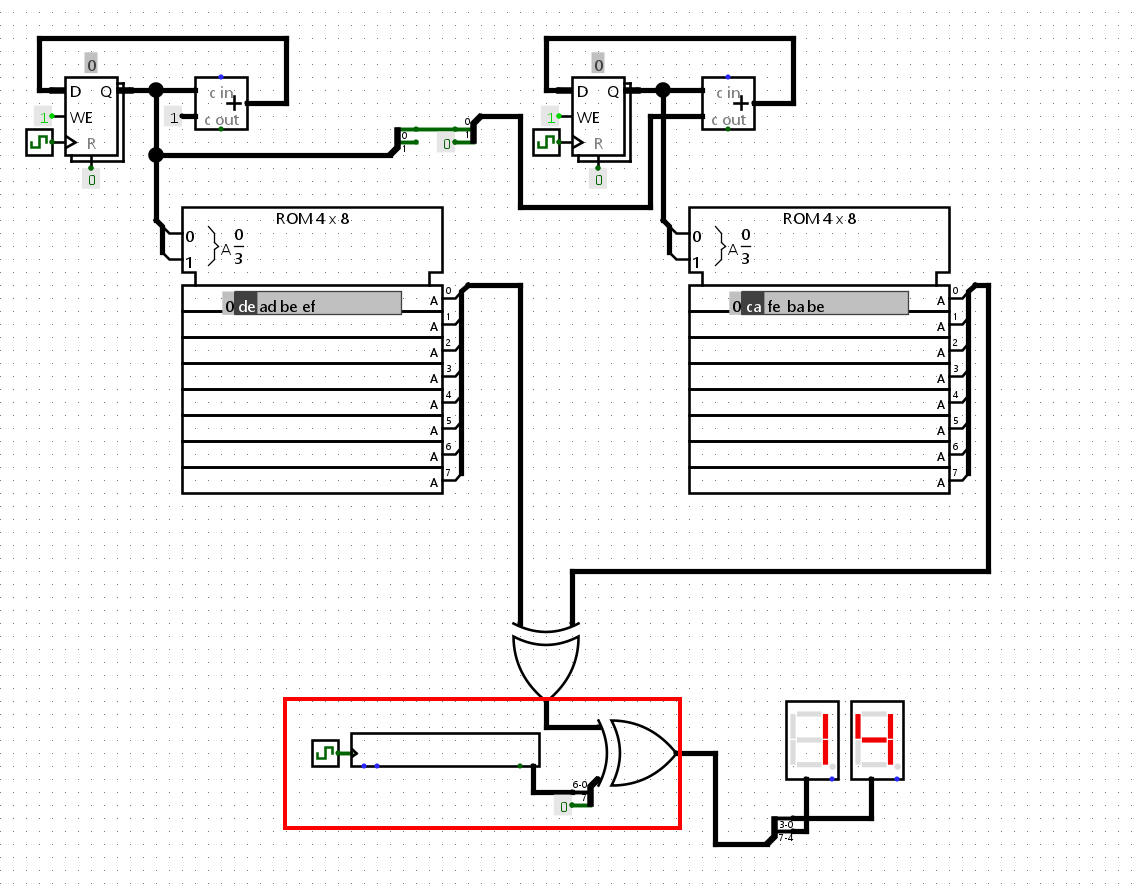
Step 2-B : Let’s remove the useless part
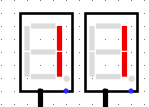
I decided to take a closer look at the schematics. Here are some interesting things I figured out. The red section is not useful in the entire process so we could just bypass it
In fact, the signal outputted by this section stays to 0 in the entire process which means that the first XOR will be XORed with 0 and therefor won’t change
Step 3 : Extracting the XOR key
Step 3-A : just a few bytes to be sure
I reloaded the file to make sure it starts fresh as I previously tested multiple clock counts to make sure I could remove a section of the schematics
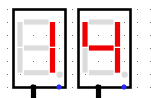
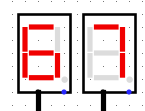
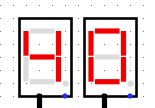
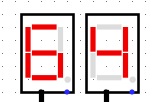
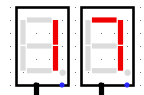
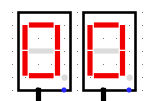
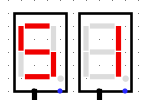
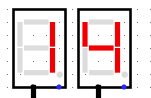
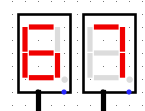
When we run the system for à few clock turns we can see it gives us different values on the 7 segments displays, if we try to XOR it with the original output given in the challenge we can see some promising results
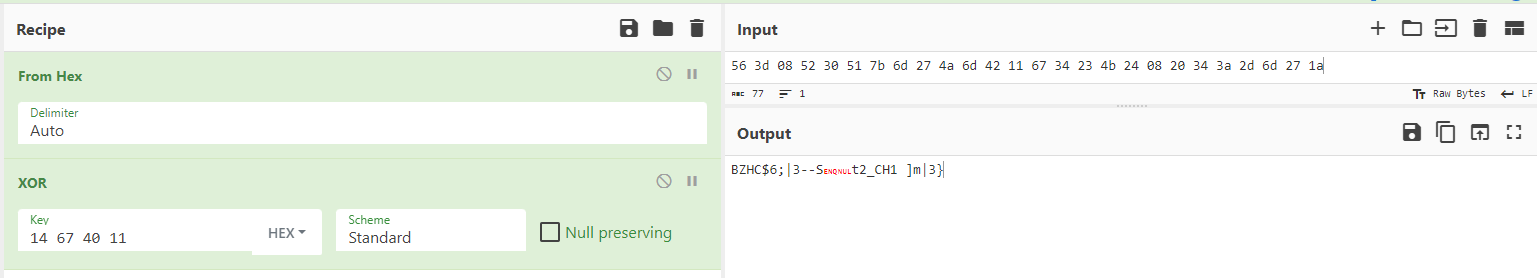
BZHCwhich is the start of the flag headersThis looks quite promising
Step 3-B : Let’s decode the message
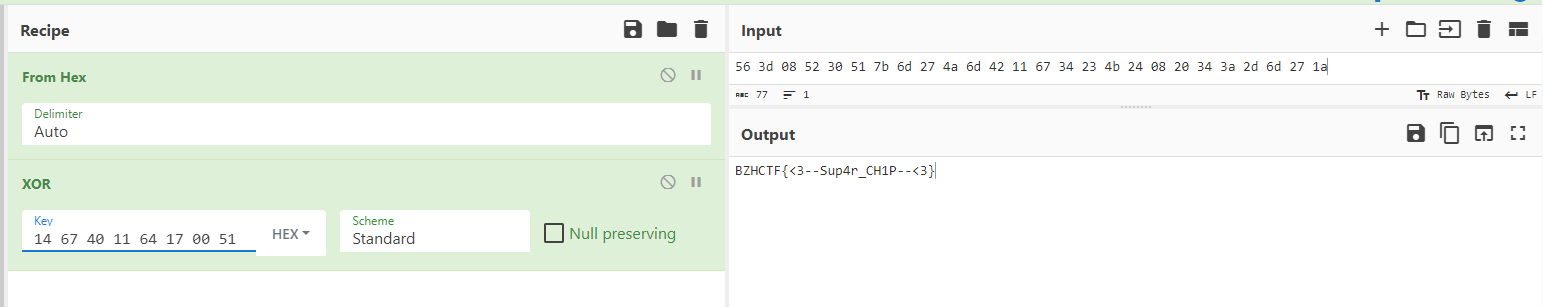
If we run the system longer, we get the entire key :
14 67 40 11 64 17 00 51After these 8 values it starts over again with the same values
Let’s put it back in cyberchef and see the result :


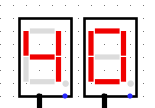
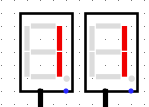
.png)